Self-Propagating Monsters
Discovering one of the world's first computer viruses
by FRED BECKHUSEN
Late one night in 1977, I stared at the programming card of a PDP-11, the influential 16-bit minicomputer sold by Digital Equipment Corporation. I was about to discover a real living “bug” in the computer and the Z-80 microprocessor. This was highly unusual as they were single opcodes, and was perhaps the third known of any virus type.
A quarter-century later, computer viruses are a scourge with no known cure — only an escalating arms race involving an array of hackers, cybersecurity giants and governments. But at that time, there were few precedents. The mathematician John von Neumann had theorized what he termed “self-reproducing automata”(.pdf) in the late 1940s. In 1971, programmer Bob Thomas of BBN Technologies created what is widely regarded as the first computer virus, the relatively benign Creeper program, which simply displayed the message: “I’M THE CREEPER. CATCH ME IF YOU CAN!”
Three years later, a virus dubbed the Rabbit appeared and which was malicious — once infecting a computer, it replicated itself until crashing the machine. A year after Rabbit appeared, the programmer John Walker developed ANIMAL, a Trojan in the form of a simple game which carried a duplicating program called PREVADE. That night in 1977, I had no idea I was about to discover what was possibly the third and fourth.
Its only purpose in ‘life’ is to procreate and eat food, namely time.
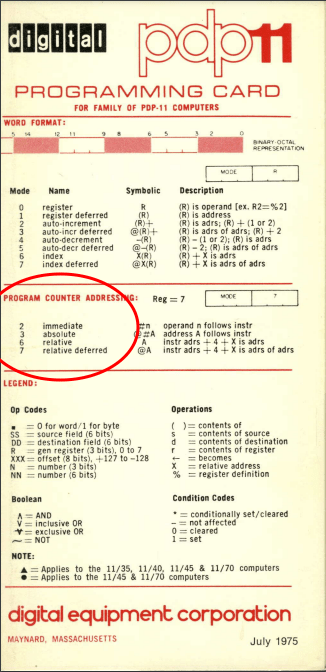
For starters, I noticed there was no documented addressing mode for 47, which is -@PC, or -(PC). Digital Equipment Corporation must have decided it was useless — a classic “undocumented instruction.” So I dug into it more deeply, and came up with a use, “014747.”
The 01 is the actual opcode for MOVE; 4 is -(Register); and the 7 is Register 7, which is the program counter. After fetch and decode, the program counter points to the next address.
The CPU microcode decrements the PC by two to point to the original 014747, and that fetches the original 014747 opcode. The program does the DD part, again -(PC) with a write cycle to the destination, which ends up writing 014747 to the memory location below the original instruction — and therefore leaving the program counter pointing to the moved instruction. It fetches and runs that new opcode.
This runs the program counter backward and fills memory with 014747.
Next, the program does an underflow trap when it decrements past location zero, so does not “roll under” and start at the top. It tries to load the vector at 014747, which is an odd address (which is illegal), so the trap within a trap halts the CPU. Otherwise, it would fill from the top of RAM down to the first opcode and repeat. This could also be done going upward with 014727, which was MOVE -(PC), +(PC), but that still used the undocumented instruction.
So I dug into the Z-80 opcode set looking for something similar, and both were published in the November 1977 edition of Byte magazine (.pdf):
SELF-PROPAGATION MONSTERS
I discovered a real “bug” in the Z-80. If the registers are set up correctly, and the user has 64 K of programmable memory, a “living” creature can be created, similar to the interrupt driven monsters that pop up unexpectedly. Its only purpose in “life” is to procreate and eat food, namely time. If you object to my use of the term “life,” go back and reread the definition. The “creature” is an ED 80 instruction, the block transfer LDIR.
To put it simply, it turns into a memory eater, copying itself everywhere into memory, perpetuating its existence. Externally, it looks like an ED 80 running loose. Here it is:
ORG 0000H
01 00 00 LD BC,0000H ;DO 65K TRANSFER
11 0B 00 LD DE,000BH ;UP 2 LOCATIONS
21 09 00 LD HL,0009H ;TO PERPETUATE
ED BO LDIR ;HERE'S THE ANIMAL
;THAT GOES RUNNING OFFTry it for fun.
Also in this category, there’s a 14747 instruction in DEC PDP-11s. It copies itself lower in memory (even though DEC manuals say the instruction shouldn’t work), and then executes the moved instruction! This one doesn’t perpetuate, but it’s neat to kill memory when you don’t want someone to screw with some secret software.
Fred Beckhusen
MS 23
Mostek Corp
1215 W Crosby Rd
Carrollton, TX 75006
Byte replied:
Then of course there is the famous MVC instruction of the IBM 360 and 370 series, key to the famous OS 360 “time bomb” technique wherein a propagating MVC in supervisor mode mysteriously clears a 360’s memory, crashing the machine hours after the joker who scheduled it has signed off TSO. Since the MVC moves 256 byte chunks and, once started it always completes, the last MVC of the program goes one step further by clearing the program itself! (Reputedly, later than the mid-1970s, releases of IBM’s TSO closed the holes by which clever programmers could get into supervisor mode from TSO terminal.). . . CH
These self-replicating monsters weren’t called “viruses” then, the term hadn’t been coined yet. But with the proliferation of desktop PCs and the internet over the subsequent decades, these automata have become as sophisticated than ever, and still happily reproducing themselves in perpetuity. In the 1970s, they didn’t spread widely but were even more surprising when you discovered one.
It was certain that computing was about to change.
Fred Beckhusen is founder and CEO of Micro Technology Services, Inc.



